Is your Vulnerability Management Tool able to detect all vulnerabilities in your network?
I got the inspiration for this post after reading this entry from Alexander Leonov. He investigates the blind spots on the Vulnerability Scanners databases, and how we may assume that any new and old vulnerability ever published will be identified by our shiny tool for which we pay a substantial license. As he explains that’s not actually true, and uses as reference the excellent CISA Known Exploited Vulnerabilities catalog.
As I have access to an updated Tenable.sc instance, I used a different approach to obtain the CVEs that are in its plugins database, I access the API to get all of them and then cross-reference them with the CISA KEV catalog.
Nessus Plugins
Nessus uses plugins to detect vulnerabilities, and all of them can be retrieved via API endpoint plugin. Why not retrieve all of them and extract the unique CVEs referenced? That will give us the complete list of CVEs that Nessus can detect at any given time.
I use PowerShell to work with the API, check these posts for an introduction on how to do that. Let’s get to it; first get all plugins from the Tenable.sc instance:
# Generate authentication headers
$accessKey = 'ACCESS_KEY_HERE'
$secretKey = 'SECRET_KEY_HERE'
$headers = @{}
$headers.Add("x-apikey", "accessKey=$accessKey;secretKey=$secretKey")
$scURL = 'https://192.168.23.12'
#Get all plugins with CVEs
$result = Invoke-RestMethod -Uri "$scURL/rest/plugin?fields=id,xrefs&endOffset=200000" -Method Get -Headers $headers -UseBasicParsing | select -ExpandProperty "response"
Next, we extract all CVE IDs from the field xrefs with some regex.
# Extract all CVEs covered by plugins.
$allCVE = @{}
# Regex expression to separate CVE IDs
$CVERegex = [regex]'CVE-\d+-\d+'
# Go over all plugins, extract CVE IDs and store them without duplicates
foreach ($xref in $result.xrefs) {
foreach ( $match in $CVERegex.matches($xref) ) {
if ( -not $allCVE.ContainsKey($match.value) ) {
$allCVE.Add($match.value, '')
}
}
}
If we want, we can save all CVEs to a file
$outputFileAllCVE = 'C:\KEV\all_CVE.txt'
$allCVE | Out-File -FilePath $outputFileAllCVE

Those are a beautiful 68466 different CVEs as of April 2022.
Enter CISA KEV Catalog
Now that we know which CVEs our scanner can identify, let’s see if there are some gaps between these and the ones in the CISA Catalog. Remember those are identified as being exploited in the wild. Download the CSV file from here, then let’s check which are not in our CVE list from Nessus.
# Get KEV from file
$kev = Import-Csv 'C:\KEV\known_exploited_vulnerabilities.csv'
# Get CVEs in KEV and not covered by Nessus
$kevNOTMatch = @()
foreach ( $cve in $kev ) {
if ( $cve.cveID -notin $allCVE.Keys) {
$kevNOTMatch += $cve
}
}
Last, I export the results to CSV for later processing
# Prepare outputfile
$outputFileKEVNotCovered = 'C:\KEV\KEV_notCovered.csv'
# export to CSV KEV not covered by Nessus
$kevNOTMatch | Export-Csv -path $outputFileKEVNotCovered -NoTypeInformation
And we get a nice table with all the vulnerabilities that our Vulnerability Scanner cannot detect at the time I ran the script. You can also find the file for reference here
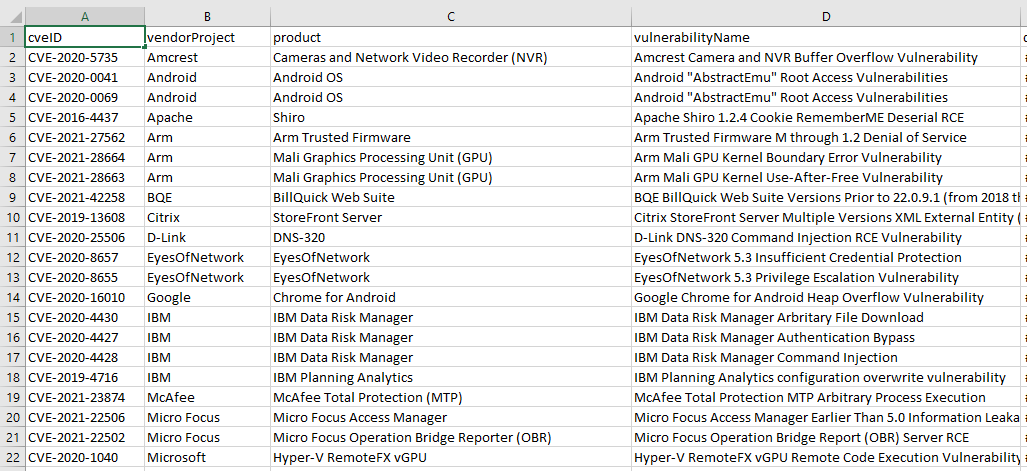
There are some enterprise products in the results, like IBM or Citrix.
Should I be worried?
Now, we know which gaps we have in our tool and we can assess if any of those missed vulnerabilities affect a product that is present in our network. I like doing this every time CISA updates the catalog to avoid unwelcome surprises 🙂. The take away for me is the same as Alexander explains in his blog, dont’ trust blindly your vulnerability scanning tool and if possible, use more than one, as I do 😉.
Find the script with all PowerShell code here