Top ATT&CK Techniques
Today I wanted to show a little bit how to use the new tool released by the Center for Threat-Informed Defense the Top ATT&CK Techniques calculator, which can be accessed here. The main purpose of the new project and the calculator is to help determining where to invest our efforts to defend our network. I you followed my series in how to improve detections with the ATT&CK Framework, you are in a perfect position to take advantage of this tool.
The idea is to obtain the top most relevant techniques that could impact your environment, based on the Prevalence - how frequently a technique is being used, Chokepoints - techniques where a high number of other techniques converge to or diverge from, and Actionability - the availability of detections or mitigations. Find all the details about the methodology here.
Calculator
The best way of learning something is doing it, so let’s give a try to the calculator; I’m going to start based on my previous posts and use the gaps I identified in my example organization. At the end of part two, I generated a navigator layer with techniques where I have visibility but no detections. See screen capture below:
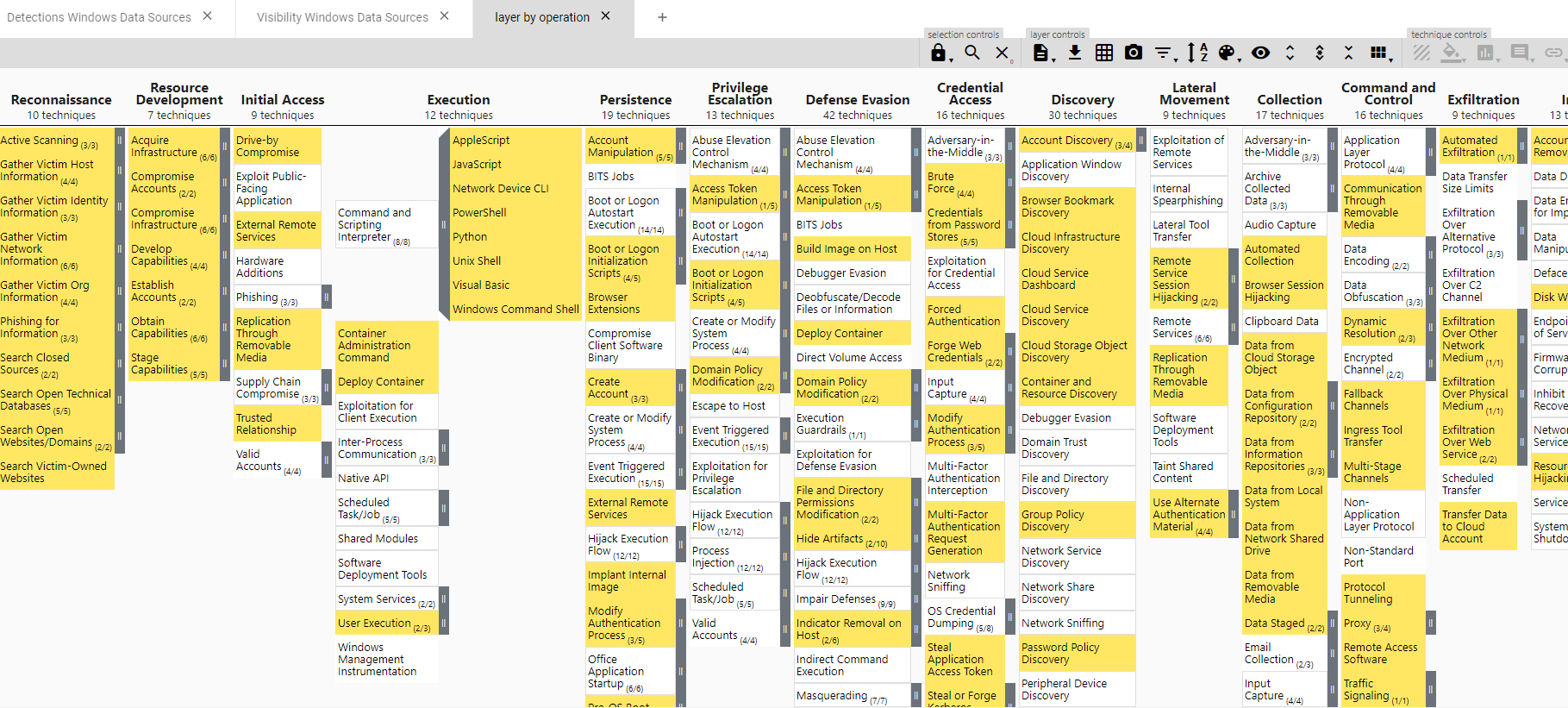
You can also get the layer JSON file from here if you want to work yourself with it in Navigator.
Following up on this one, we see a lot of yellow, which in this case means a lot of opportunities to add detections; but where to start, right? We’ll use the web calculator to give us a good idea on where to focus now, based on the knowledge we gained in our previous work.
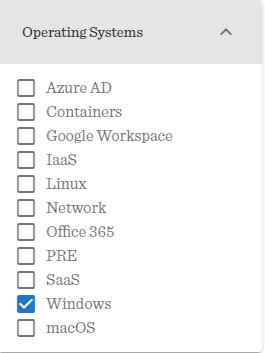
First, from the filters, I’ll select the platform Windows, as it’s where I worked so far:
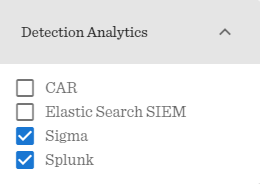
From Detection Analytics I’ll select Sigma and Splunk, as I assume that those are the ones useful in my example. I leave out NIST and CIS controls for now - they help narrow down our focus to specific controls; we keep it simple for starters.
Now, let’s say I want to start working on those Scheduled Task/Job(T1053) sub-techniques, where I know I have a good visibility thanks to Sysmon logs, and I think is my best candidate to start working on.

Let’s toggle the filters so the weighting applied by the tool plays in our favor; I mark Network and Cloud Monitoring Components as high, so their weight will be lower and they don’t show up in the list; this may seem counter intuitive, but as I want to focus in Process Monitoring, I want its weight to be the highest, so I leave the filter for it and File Monitoring at None. Also, as we discovered before, we have good visibility of those but not detection analytics, which is what we are looking to improve.
Click in Generate Results
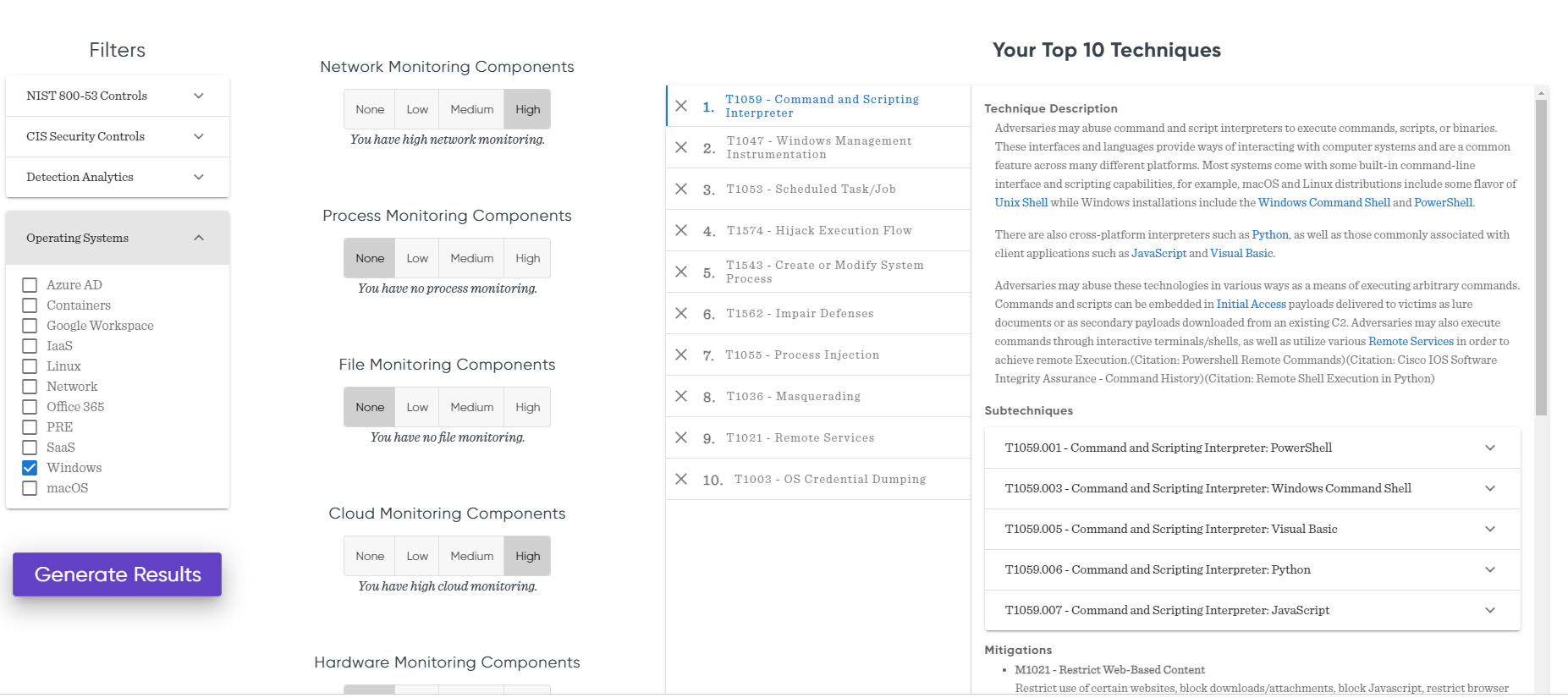
This gives us a list of the most prevalent and actionable techniques according to our filters. Those would be a great point to start, and it’s a much more manageable task.
We see T1053 in 3rd place, which means is a very good candidate to focus our attention, as expected, but not the best one according to the criteria used in the calculator. We already see the data challenging my initial assumption. At this point I could decide changing my priority and start looking at analytics for T1059, as it’s the first in the list.
But we might have internal data thanks to pentest or redteaming exercises (Scheduled task technique being used and not detected during the exercise), or from previous attacks where adversaries used a specific sub-technique like T1053.005 that indicates that T1053 is still our first priority; and as it’s in the list, we know that the sub-techniques included will have good mitigation and detection analytics available.
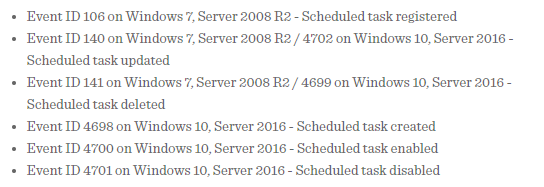
If that’s the case, we can go to the Detection section on sub-technique T1053.005, and see some concrete suggestions for Event IDs to monitor for detection:
Conclusion
As I initially explained, this is a very good tool if you feel overwhelmed by the high number of techniques to cover, specially if you are starting this process or you are part of a small team with not much resources to invest. It’s not perfect, and of course the Center for Threat-Informed Defense acknowledges this at the end of their methodology document on the Limitations section, which is worth a read as well.
If you start working following this list, you know you are fixing prevalent techniques that will have good opportunities for mitigation and detection, and they are bound to cause disruption to attackers. What’s not to like?
If you want to let me know what you think about this new product and ideas on how to use it, you can find me in Twitter at @cibermanchego and in LinkedIn.