This is the second part of my walkthrough for the Splunk Corelight CTF, you can fin the first part here. You can find the CTF in Splunk’s BOTS site.
SPOILER ALERT: I INCLUDE ALL THE ANSWERS TO THE CTF, BUT HIDDEN, SO YOU HAVE TO CLICK TO SEE IT, IN CASE YOU WANT TO PLAY ALONG
Now, let’s play the second scenario.
Scenario 2
Important: use for this scenario the index “ctf”
-
An HTTP request is made to a specific PHP page. What is the filename of that page (excluding any path or slashes)?
We just look at HTTP logs and PHP files in the uri field:
index="ctf" path=http uri=*.php | stats values(uri)There is only one value as result, that is our answer.
Answer (Click to Expand)
whoami.php
-
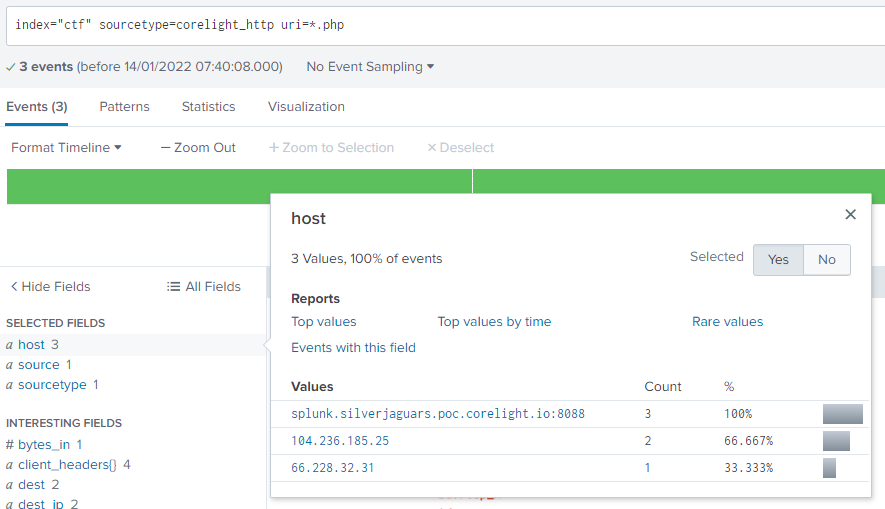
What is the IP address that only appears once as the server for the three connections in the previous question?
We repeat the search:
index="ctf" path=http uri=*.phpAnd in the host field find the answer.
Answer (Click to Expand)
66.228.32.31
-
What is the IP address that mail.ventascintas.com resolved to?
Let’s look at the DNS path in the logs searching for that host:
index="ctf" path=dns mail.ventascintas.comOnly 1 event, look at the field answer
Answer (Click to Expand)
142.4.4.112
-
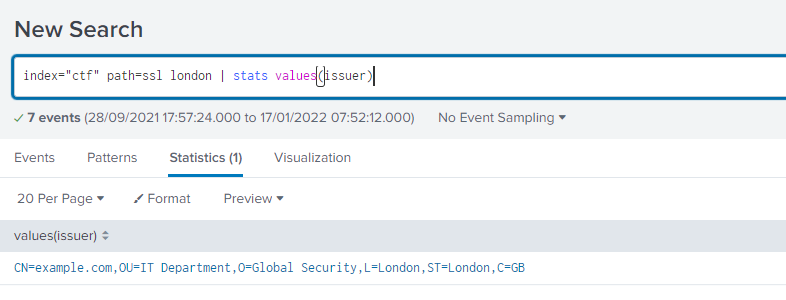
What is the domain associated with an X.509 certificate subject that purports to be from London? Answer guidance: Provide the domain name of the system. Example: splunk.com
Let’s look at the SSL path in Corelight logs:
index="ctf" path=ssl london | stats values(issuer)Only one result, with our answer there.
Answer (Click to Expand)
example.com
-
What cipher suite was used with the certificate from the prior question?
The field ssl_cipher has the answer:
index="ctf" path=ssl london
Answer (Click to Expand)
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
-
There is a unique JA3 hash associated with certificate from the previous question. What is that hash?
Field ja3 from the events above.
Answer (Click to Expand)
35492f143de0f906215ea3aaf6ee0a74
-
What was the matching JA3S hash associated with the JA3 hash identified in the previous question?
Again, field ja3s
Answer (Click to Expand)
f2e1706526fe0692ee36be58110ffc83
-
What department does that certificate from question 204 allegedly correspond to?
Still in the same events, we find the answer in the OU part in the certificate Subject.
Answer (Click to Expand)
IT Department
-
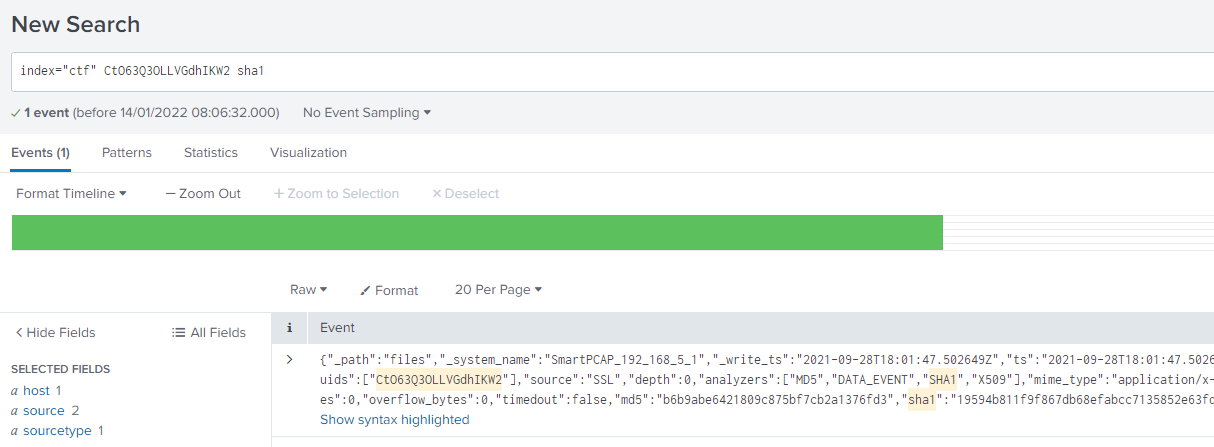
What is the SHA1 of the most recent X.509 certificate from question 204?
We need to find a path where sha1 hashes are stored, as the ssl doesn’t have them. We use the UID of the most recent event and look for sha1:
index="ctf" CtO63Q3OLLVGdhIKW2 sha1There is only one event, from sourcetype corelight_files and there is the sha1 field.
Answer (Click to Expand)
19594b811f9f867db68efabcc7135852e63fd7da
-
An executable was downloaded from 124.158.6.218. What was the name of that executable?
We look for the IP and in the sourcetype we used in previous question, corelight_files:
index="ctf" 124.158.6.218 sourcetype=corelight_filesIn the field filename we see the answer
Answer (Click to Expand)
i5pv72yr.exe
-
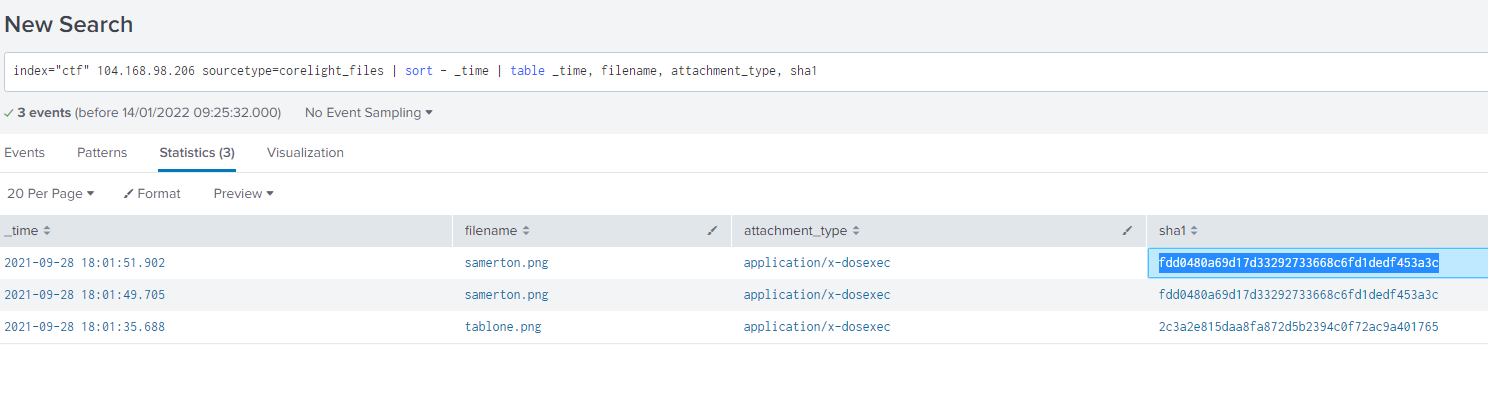
As part of this traffic, there were two executables downloaded from 104.168.98.206. What is the SHA1 of the most recently downloaded executable?
Again we look at sourcetype corelight_files, look for that IP, and sort by time for the most recent first, make a table with filenames, file type and SHA1 hash:
index="ctf" 104.168.98.206 sourcetype=corelight_files | sort - _time | table _time, filename, attachment_type, sha1
Answer (Click to Expand)
fdd0480a69d17d33292733668c6fd1dedf453a3c
-
There was a Word document downloaded that has some Spanish flair to it. What was that document’s name?
Well, this one should be easy for me 😉. We look for files with extensions .doc or .docx, get individual hits with dedup and display file names:
index="ctf" sourcetype=corelight_files (filename=*.doc OR filename=*.docx) | dedup filename | table filename, attachment_typeOnly 4, one with a Spanish word on it.
Answer (Click to Expand)
Archivo 18-09-2019_23119.doc
-
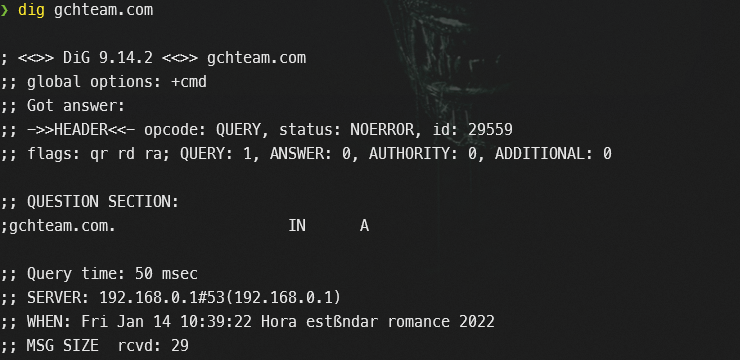
There’s an email address sending suspicious emails from a domain that no longer resolves to an IP address. How many emails were sent with that email address?
We can start by looking at events in corelight_smtp:
index=ctf sourcetype=corelight_smtp | table mailfrom, subjectOnly 2 email addresses: jobs@hitmail.cc, crogstrike@gchteam.com. If we run a dig query for both domains, we see one not resolving any IP
Let’s find out how many emails were sent from that address:
index=ctf sourcetype=corelight_smtp mailfrom=crogstrike@gchteam.com
Answer (Click to Expand)
35
-
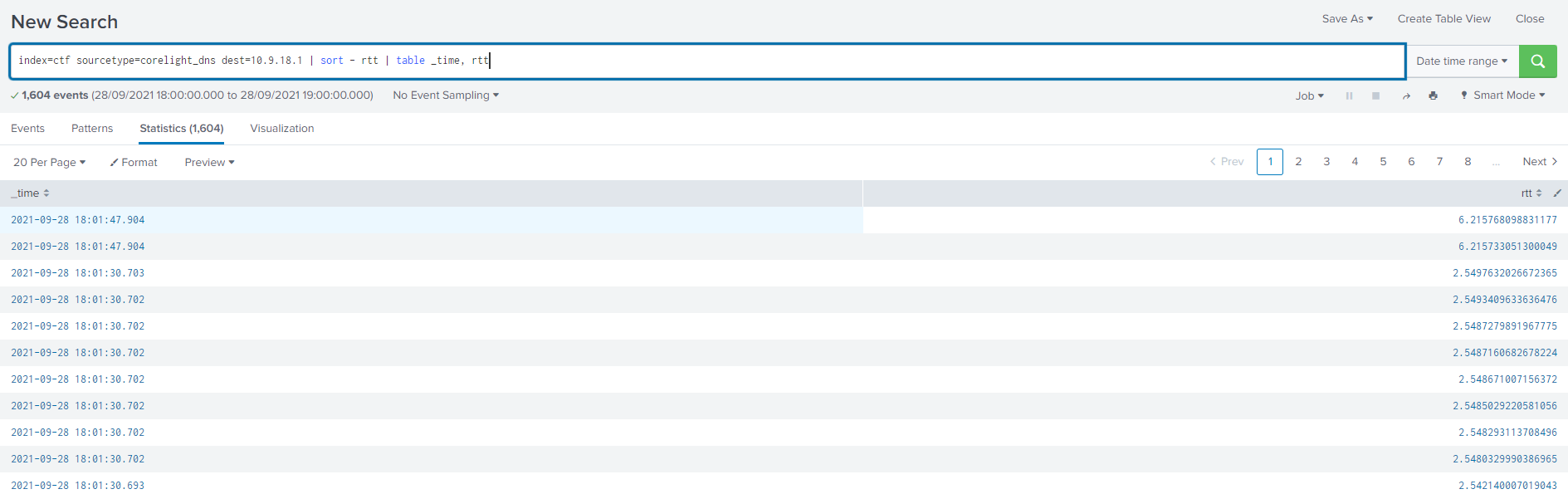
What was the average time between a DNS request and a DNS response for the DNS server with the IP of 10.9.18.1?
This one is a bit more challenging, and it plays with the concept of RTT(Round Trip Time) applied to DNS, which is the time spent from when the DNS query is sent and the answer is received.
To find the answer, first we find DNS requests to that server:
index=ctf sourcetype=corelight_dns dest=10.9.18.1Then, we need to look at field rtt which is the Round Trip Time of a DNS request, make the AVG and round to 5 decimals:
index=ctf sourcetype=corelight_dns dest=10.9.18.1 | stats avg(rtt) as avg_rtt | eval avg_rtt=round(avg_rtt,5)
Answer (Click to Expand)
0.16123
-
This traffic sample has been reduced to a four minute window, during which we observed unusually high delays on DNS responses. During what minute were DNS responses slowest?
Here I went a bit crazy as I was putting the correct answer but with a 0 in front. The solution is not difficult though.
If we reverse sort by rtt, we’ll get the highest values first, looking at the time of those, we can see the minute that delays in responses happened just looking at the field _time:
index=ctf sourcetype=corelight_dns dest=10.9.18.1 | sort - rtt | table _time, rttA more exact approach would be grouping rtt by 1 minute slots with bucket command and then calculating the average:
index=ctf sourcetype=corelight_dns dest=10.9.18.1 | bucket _time span=1m | stats avg(rtt) by _time
Answer (Click to Expand)
1
-
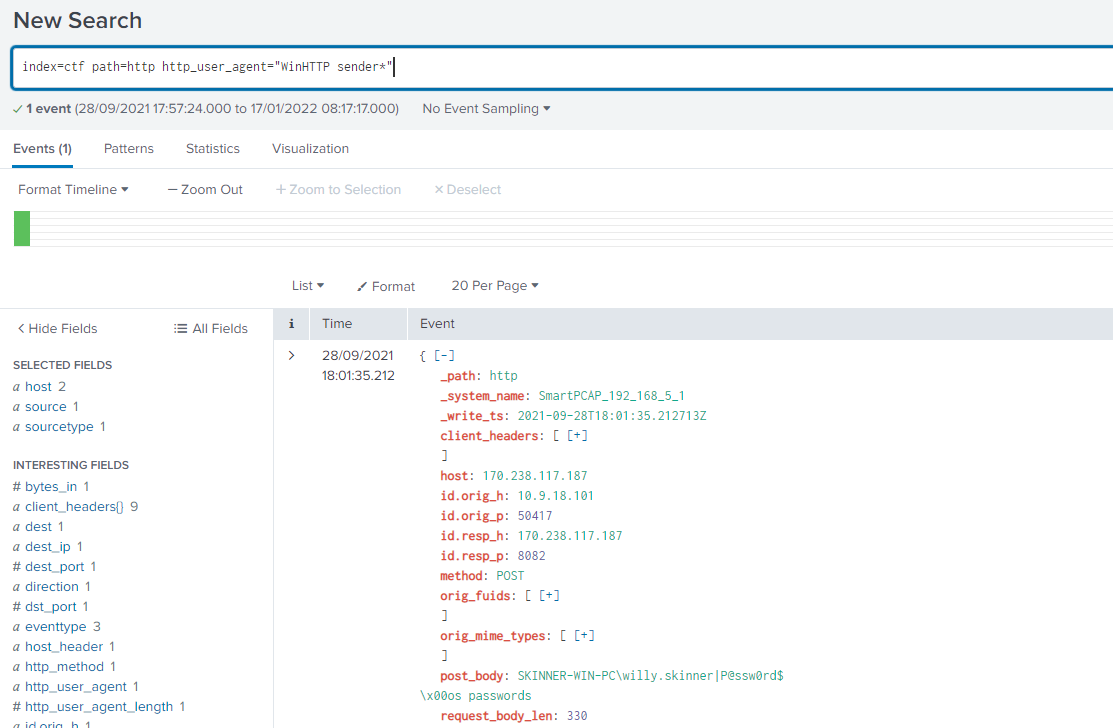
An analyst was reading an introduction to threat hunting and came across a User-Agent string that looked familiar: “WinHTTP sender”. What is the hostname of the infected host?
We look straight away for that User-Agent in HTTP logs:
index=ctf path=http http_user_agent="WinHTTP sender*"Only 1 event. From here we get the source IP, which is the infected host: 10.9.18.101. But we need the hostname. In the post_body field we see the details of the host being sent, and hostname is there.
Answer (Click to Expand)
SKINNER-WIN-PC
-
In their copious free time, an analyst reads a blog post about a technique that attackers use to download files from their C2 server. A potential indicator is that the user agent will contain “WinHTTP loader”. What is the file size of the payload downloaded using this technique?
Let’s find events with that User-Agent:
index=ctf sourcetype=corelight_http http_user_agent="WinHTTP loader*"We get 2 events for 2 different file names, samerton.png and tablone.png If we look at the files path, for any of them, we see in the bytes field the same value:
index=ctf path=files (tablone.png OR samerton.png)
Answer (Click to Expand)
557056
-
Oh, here’s a hypothesis to test during our next threat hunt. Find traffic that Corelight identifies as SSL, but is actually on TCP port 80. Using this hypothesis, identify any suspicious traffic and extract the JA3S hash for further analysis.
We look at SSL logs with destination port 80, and show JA3S values:
index=ctf path=ssl dst_port=80 | stats values(ja3s)
Answer (Click to Expand)
e35df3e00ca4ef31d42b34bebaa2f86e
-
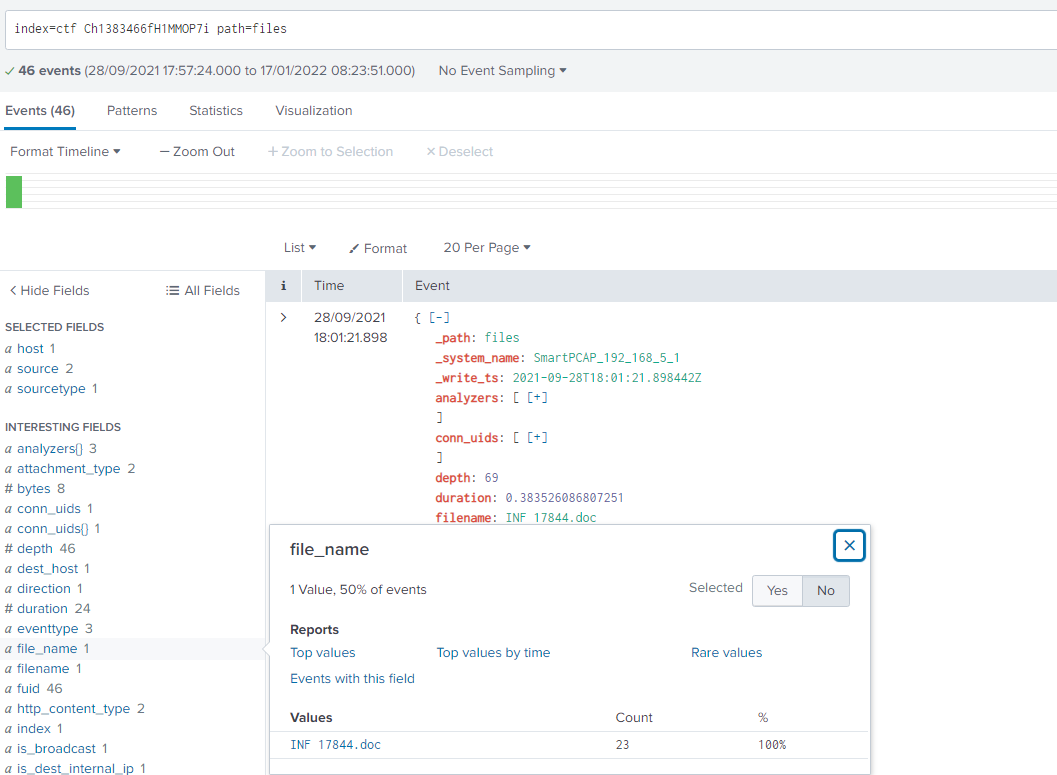
We’ve received a report that our network is sending malicious emails, but they provided the external IP address which isn’t very useful since our network implements NAT. They said the malicious email was sent to accounting@ashlinetransportation.com. Locate the email, find the attachment, and get the filename so we can statically (and dynamically) analyze its contents.
Simple search:
index=ctf accounting@ashlinetransportation.comWe get 1 event, extract the UID from there: Ch1383466fH1MMOP7i. And in the files logs we find the file name:
index=ctf Ch1383466fH1MMOP7i path=files
Answer (Click to Expand)
INF 17844.doc
-
One of our analysts is considering having a reverse engineering team take a look at an odd executable with a SHA1 hash of 026064006b987ed951ffce4f03c4394f557bf588. Use Corelight’s built-in file analyzers to identify the timestamp when the executable was complied. Answer guidance: Provide the date/time in the format YYYY-MM-DDTHH:MM:SS. Example: 2021-09-29T11:37:52
To answer this one, you need to know a little about how Corelight works and their analyzers.
Whe look in the files path for that SHA1:
index=ctf path=files 026064006b987ed951ffce4f03c4394f557bf588We see the name of the executable and that has been sent to the PE Analyzer of Corelight.
To find it in the path=pe wee need the file ID, from field fuid:
FgY7in4PHFNMPdcnC2Now we search for that value and show the compile time:
index=ctf path=pe FgY7in4PHFNMPdcnC2 | table compile_ts
Answer (Click to Expand)
2019-09-18T05:47:11
-
Before sending the file for dynamic analysis, your interest is piqued. What is the malware family for the file with hash 026064006b987ed951ffce4f03c4394f557bf588?
Go over to VirusTotal, search for the hash and look at the comments.
Answer (Click to Expand)
Emotet
Conclusion
As I mentioned at the start, this is an easy one. If you think you are ready, try the BOTS challenges, BOSS of the SOC, starting with version 1, which is a bit more accessible. I’ll probably make a walkthrough for some of them as well, they are way more fun 😊.