See part 1 of this series here
See part 2 of this series here
Prioritizing new detections
Today we continue our journey to improve our network detections. The next step is incorporating real-world threat data. Last time, we got an ATT&CK navigator layer where we identified which TTPs we have visibility but no detections. You can see the results with this JSON layer. This is just an example, not based in reality, although I’ve seen similar scenarios in real life :).
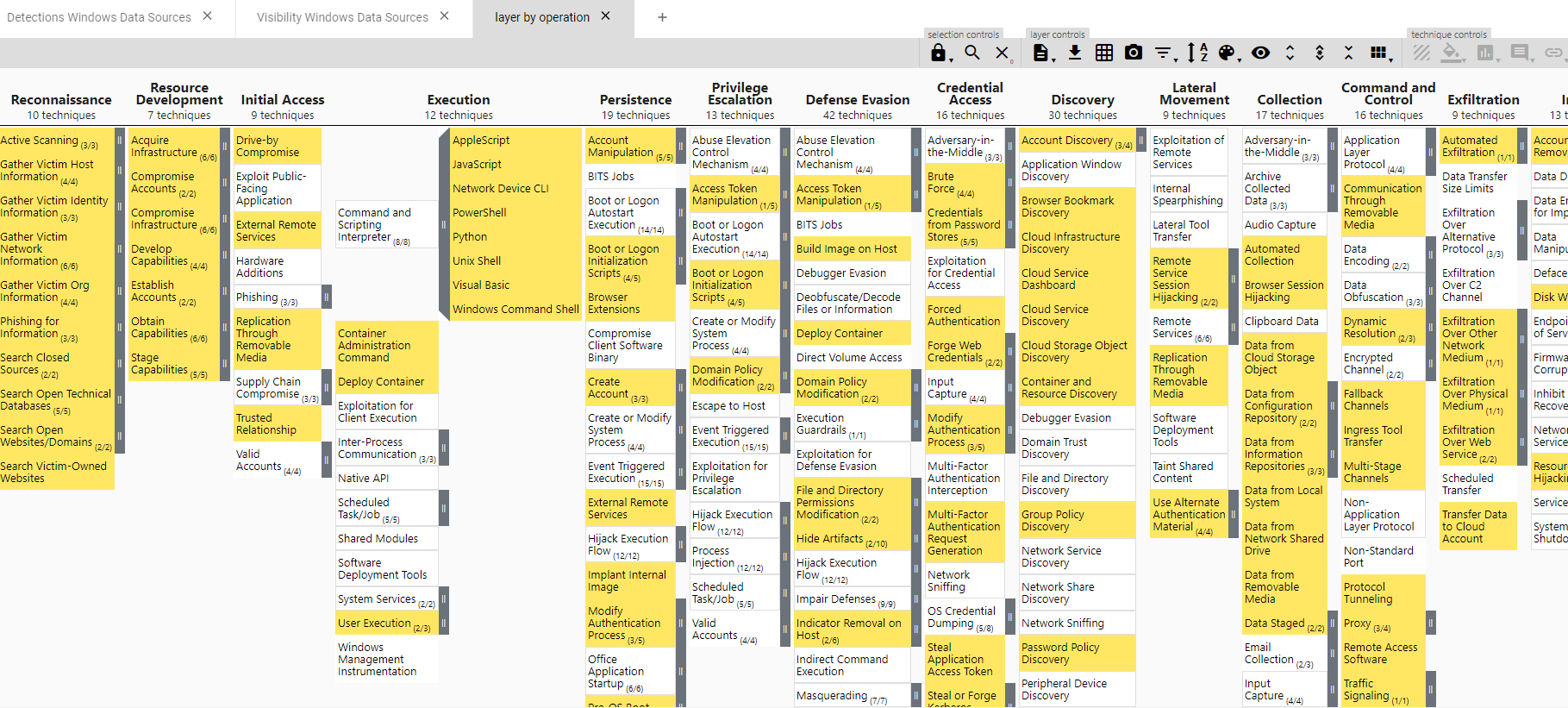
There is a lot of yellow, that means a lot of opportunities to develop detections analytics, but where do we prioritize? Enter Threat Informed Defense, we are going to use ATT&CK threat information to identify priorities based in our example company area of operations. Let’s say we are trying the defend the network of a bank, we can go to the ATT&CK website and find which threat actors are known to have compromised banks in the past.
ATT&CK Groups
With our visibility and no detections layer open in ATT&CK navigator, let’s find which threat groups we should care about. Go to groups and search for the text bank.
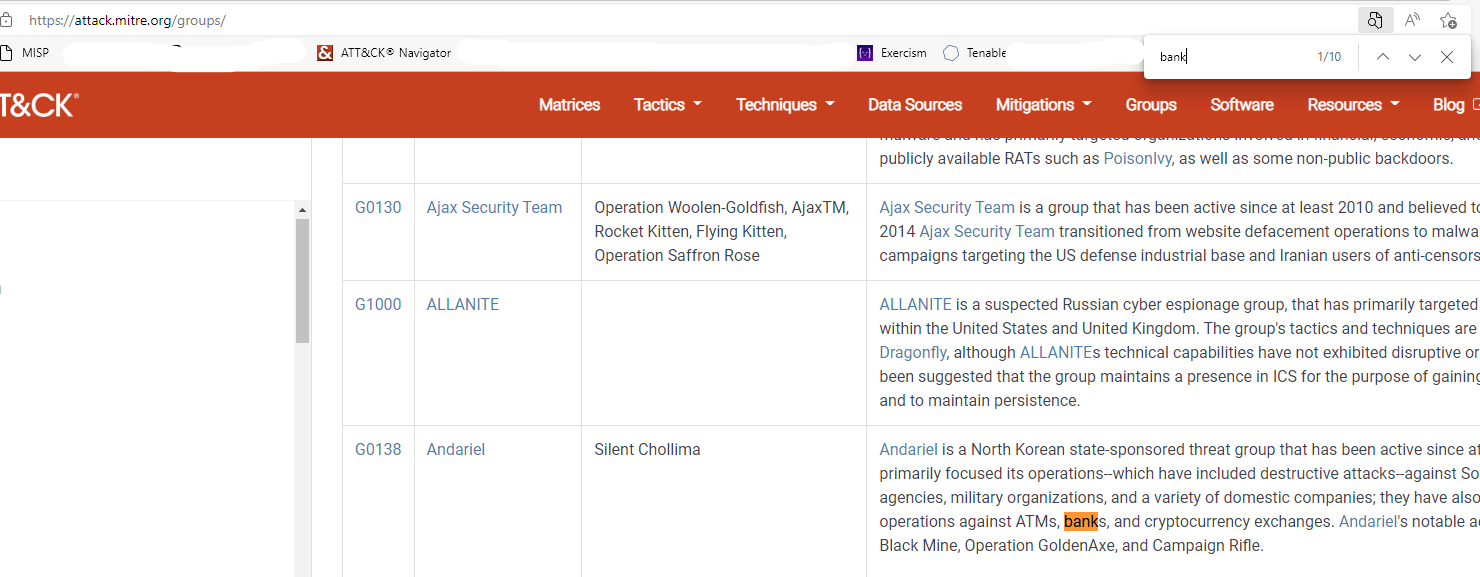
We have 10 hits, where we find references of groups attacking bank institutions; this doesn’t mean that these are the only groups targeting banks, but it’s a very good starting point. Let’s create different layers for them in the navigator.
We see that the first hit is the group Andariel. We open a new empty layer in the navigator, go to Search -> Threat Groups and select Andariel, then change the name to the layer to have the same name. Also give it a score of 1 - this will assign a color - it’s not important at this point, we’ll change that later.
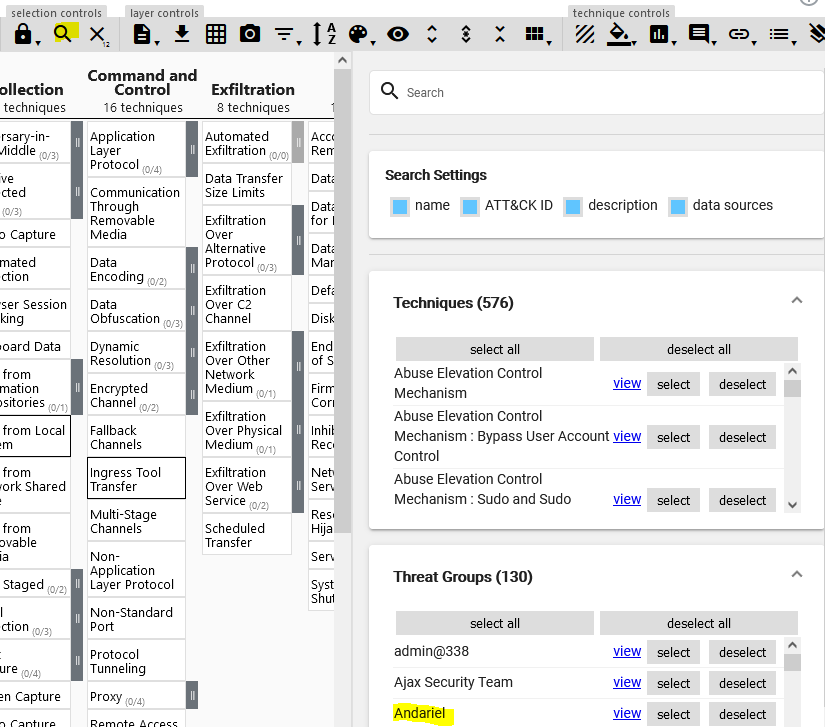
We go to the next group targeting banks, in this case APT38, and proceed in the same manner; open an empty layer, search for the group, change the name and assign a score.
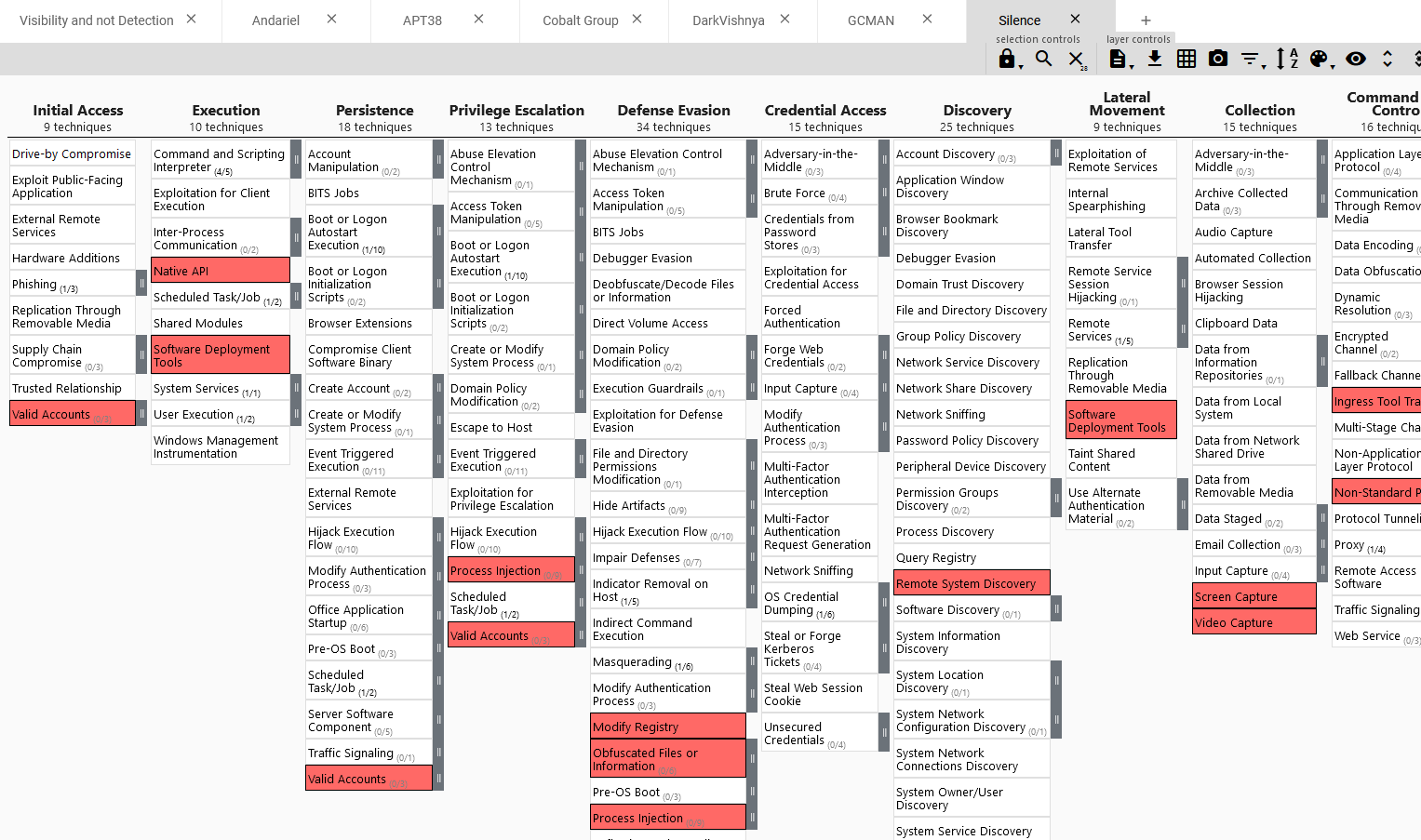
We continue the process and add all groups that ATT&CK has identified targeting banks; Cobalt Group, DarkVishnya, GCMAN and Silence complete the list.
Threat assessment for bank institutions
Now, let’s see which TTPs are more prevalent among these groups. As we did in the previous post, we can combine all the group layers to see how the stack up. Create a layer from other layers, and we sum all the groups.
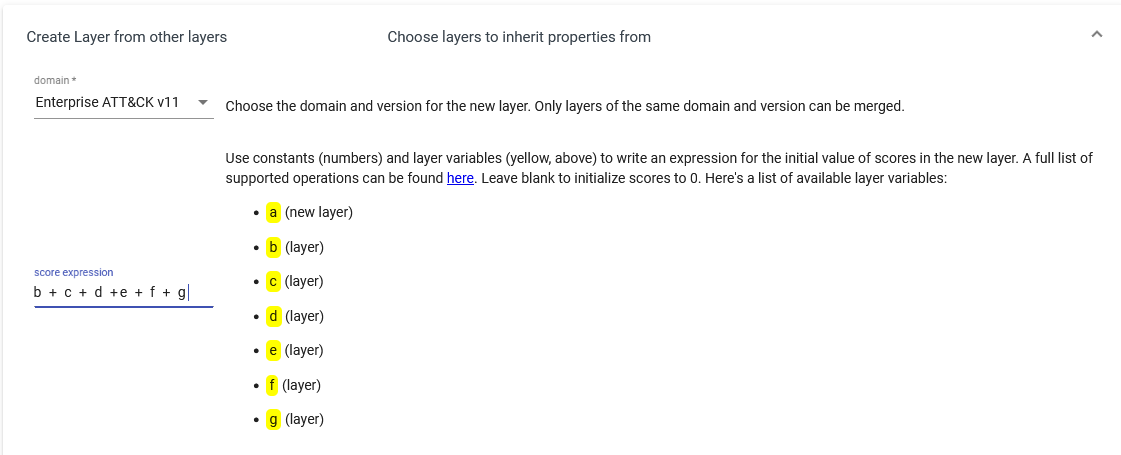
I also change the color palette to reflect the data, as the highest score for a technique is 4, I set 4 colors from light to darker - any color is fine.
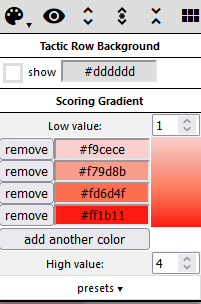
This gives us a heatmap where TTPs more prevalent get a darker color. If you want to try it yourself, get the JSON file here.
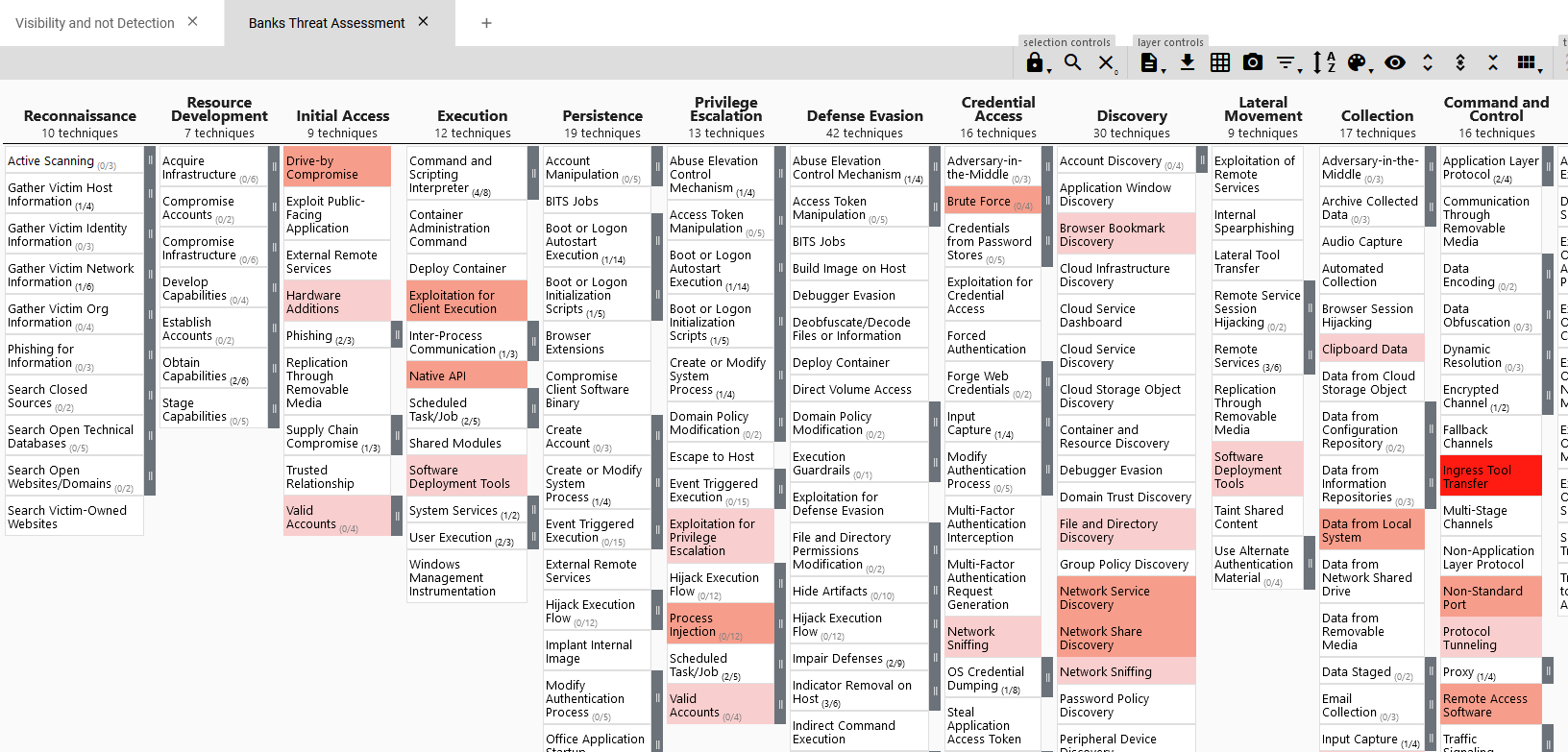
We can also expand the sub-techniques and see that they are also colored according to number of groups using them.
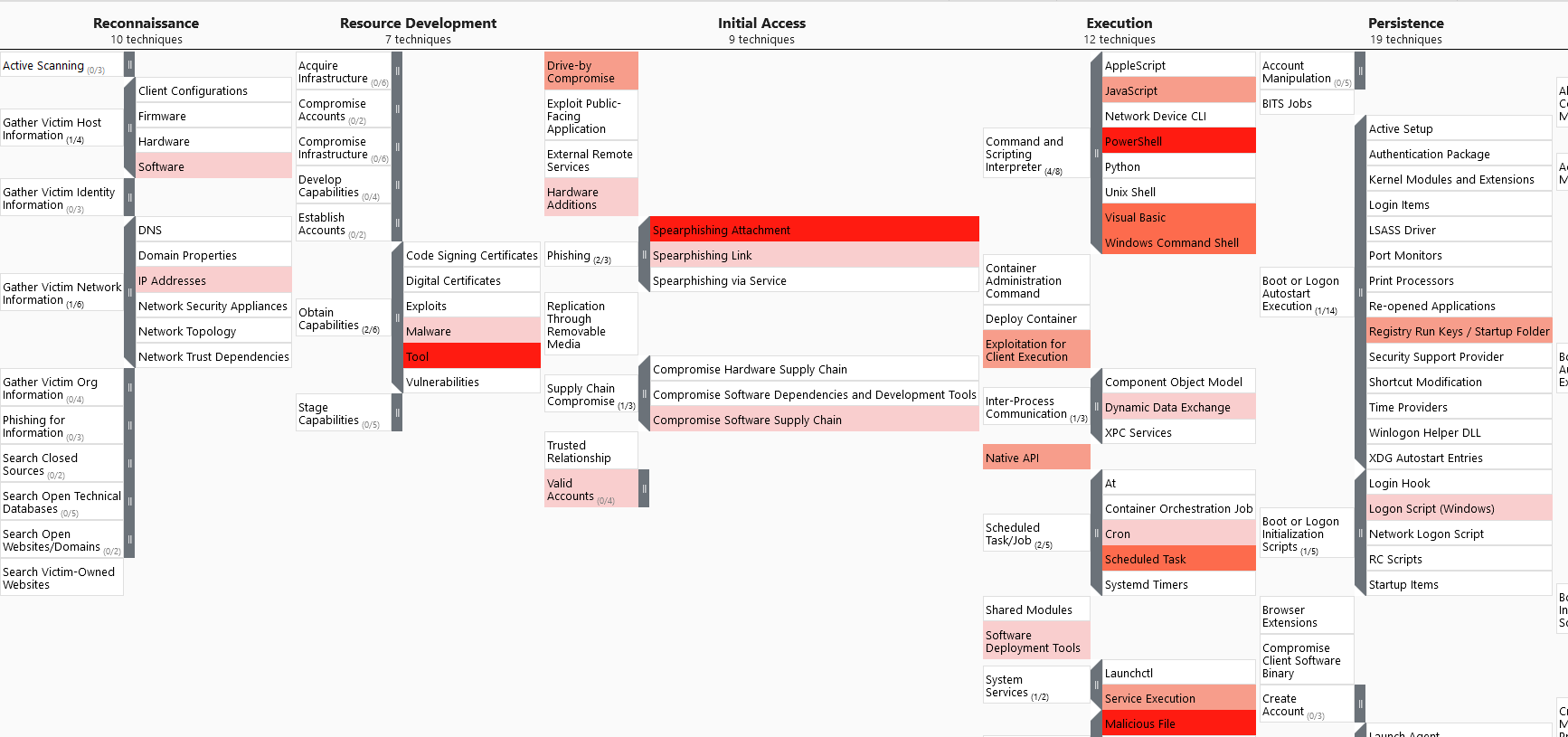
We have to take in account that this is not of course a complete list of TTPs being used against banks, but it gives us a good indication based in real-world data of where to focus our efforts. Here of course we could add more layers based on our own internal intelligence - like attacks suffered in the past - or any paid CTI services we have.
Where are my Gaps?
This is a threat assessment for any bank, now let’s see if we can find the gaps in our network for defending against these threats. We can use the layer with our visibility with no detection and combine it with the bank threats heatmap. Follow again the process of Right click -> Select annotated -> Score -> give a score of one for both layers, then create a New layer from other layers and use the expression a & b.
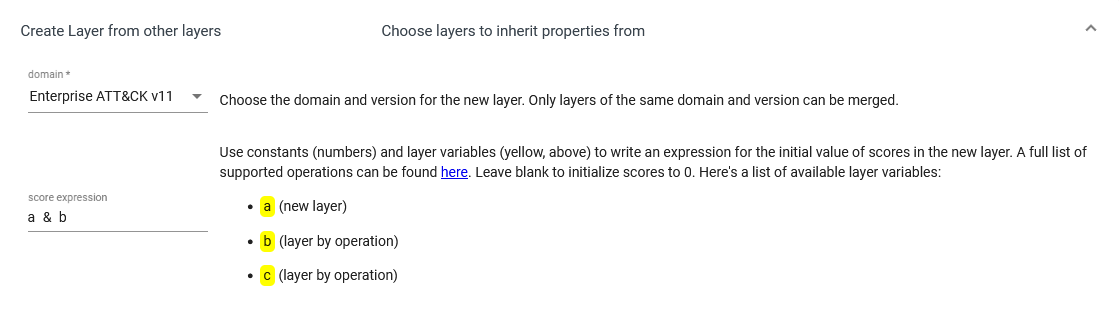
Click in Create and we get a heatmap with threats TTPs targeting banks where we have visibility and no detection yet.
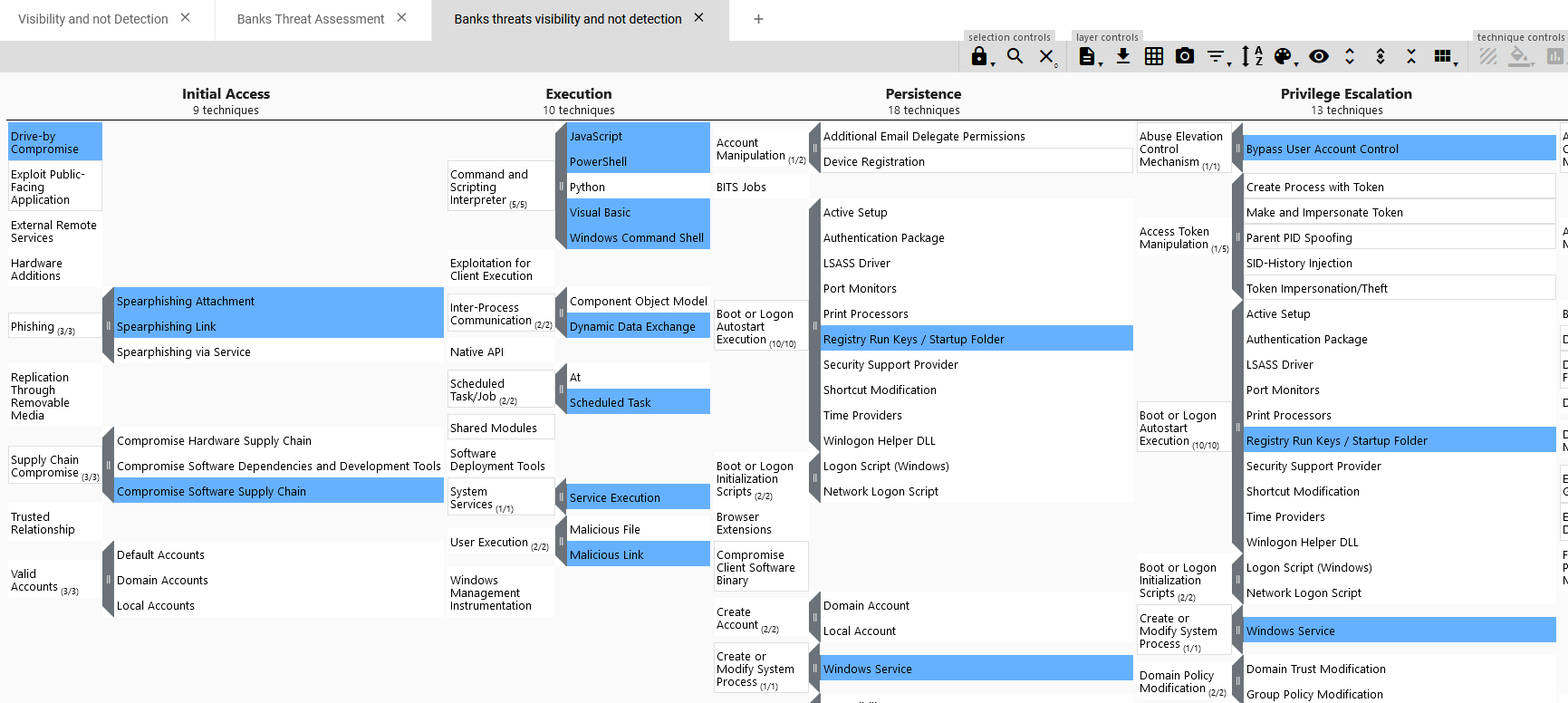
For instance, Command and Scripting Interpreter subtechnique, *Powershell(T1509.001), has a very high prevalence in our threat assessment layer - 4 of 6 groups have used it - with no detection analytics in our network; I’d say that’s a perfect candidate to focus our efforts. Take a look for yourself with my example JSON file here.
Future posts
Today we have seen how to use the concept of Threat Informed defense in our network only with opensource resources. It’s not a perfect solution but I think it’s a very good starting point, and the concept is valid to work with paid CTIs as well.
In future entries I’ll talk about Threat Emulation and how to prepare a plan to test our detections and mitigations, again based on opensource resources and real-world threat intelligence.
Hasta la vista!