This article written in collaboration with my colleague and friend Iago
From FakeCaptcha to Infostealer
What is the fake captcha attack vector?
For the last few weeks we have seen a high incidence among our customers of an attack vector known as FakeCaptcha or Clickfix. It’s currently on the top lists of most active malware families.
This technique is mainly used by infostealers like Lumma and delivered via malvertising campaigns and redirectors.
Tries to convince users that they are presented with a legitimate captcha to prove their are not a bot with a deceptive Pop-Up. Displays some variant of the typical message “I’m not a robot”.
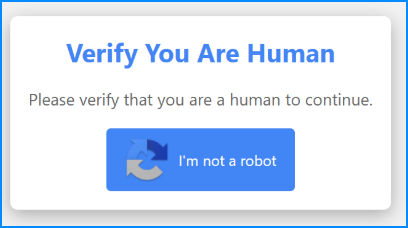
Classic captcha pop-up used in the attack.
Then victims are guided through 3 steps to ‘verify’ they are humans. What is really happening is they are copying the malicious PowerShell script from the attacker’s page and running it via the Run dialog in Windows.
-
Press Windows Key + R: This opens the Run dialog box.
-
Press Control + V: Pastes the preloaded code from the website’s virtual clipboard
-
Press Enter: Executes the pasted command. This triggers the download and execution of the initial stage payload.

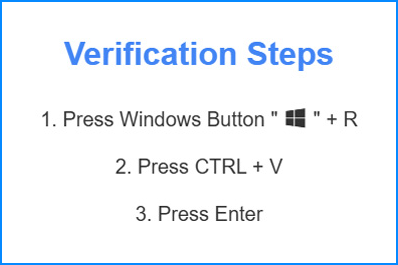
Fake captcha verification steps presented to potential victims
There are already plenty of articles explaining in detail this attack technique, we want to focus on prevention and will now explain some mitigation steps to protect your environment from this technique and avoid user to ever being able to execute the initial payload.
Mitigation
We present 2 different options to prevent users from following the fake verification steps that end up on the initial payload being executed, blocking the attack at a very early stage.
Via Group Policy
It is possible to use GPOs to mitigate the actions required by the threat actors:
- Open Group Policy editor with the gpedit.msc
- Browse to User Configuration -> Administrative Templates -> Start Menu and Taskbar.
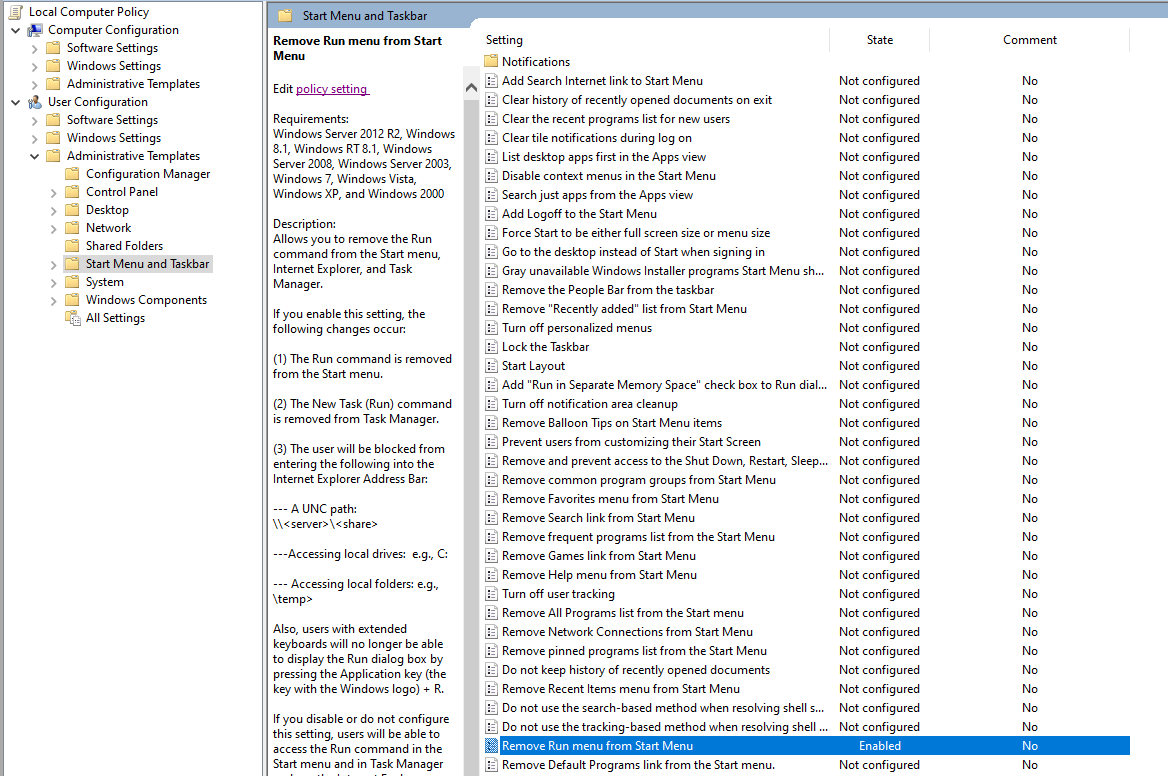
- Once there, double click over Remove Run menu from Start menu, select enable and apply
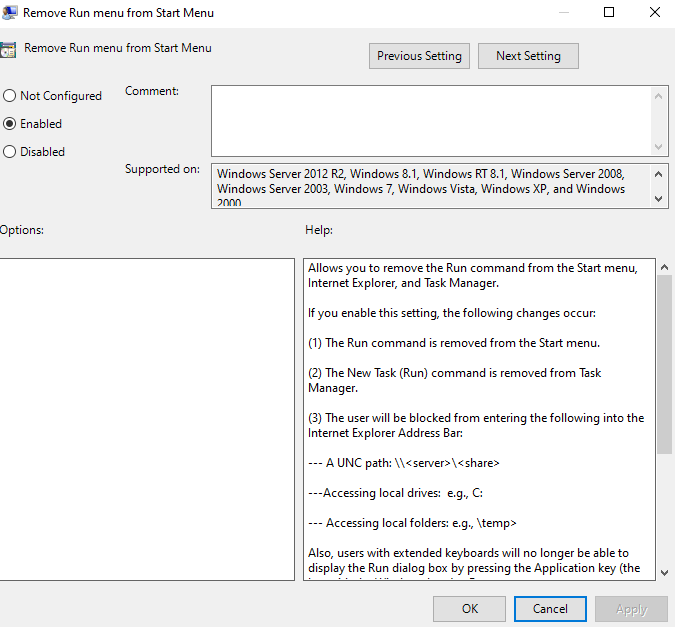
This modification will remove the “run command” from Start Menu along with some other options to open that dialog box:
Allows you to remove the Run command from the Start menu, Internet Explorer, and Task Manager.
If you enable this setting, the following changes occur:
(1) The Run command is removed from the Start menu.
(2) The New Task (Run) command is removed from Task Manager.
(3) The user will be blocked from entering the following into the Internet Explorer Address Bar:
- A UNC path: \\<server>\<share>
- Accessing local drives: e.g., C:
- Accessing local folders: e.g., \temp>
Also, users with extended keyboards will no longer be able to display the Run dialog box by pressing the Application key (the key with the Windows logo) + R.
After changes are applied, if someone tries to open Run command dialog from Start Menu with Windows Key + R, they will get the following message:
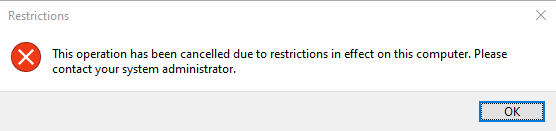
Via Registry Key
- Open the Registry Editor.
- Browse to HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer
- Add a new value as follows:
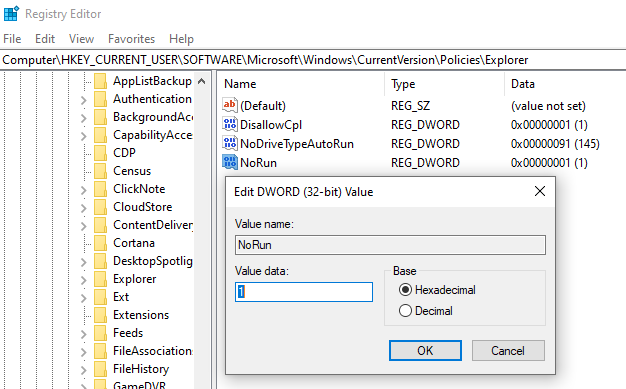
- This will have the same effect as the GPO and will prevent users from opening the Run Command dialog box.
Conclusion
Fake-Captcha or ClickFix technique has proved to be very effective on initial infections for infostealer malware. This poses a significant risk to organizations. These mitigation steps are effective and relatively easy to apply and shouldn’t affect the daily work of regular users that are the more likely to fall for these fake captcha pop-ups.
References:
Authors:
Iago, cibermanchego