BRabbit
This is the walkthrough for this Cyberdefenders lab: https://cyberdefenders.org/blueteam-ctf-challenges/brabbit/
We download the EML file from the site.
It’s an email, but we can open the .eml file with a text editor like VS Code
Locate the attachment, that is base64 encoded and convert to binary:
cat ransom.txt | dos2unix | base64 -d > ransom.bin
This is the MD5 for the attachment: fbbdc39af1139aebba4da004475e8839
This can be found in VT for instance
Now let’s start answering the questions.
Q1. The phishing email used to deliver the malicious attachment showed several indicators of a potential social engineering attempt. Recognizing these indicators can help identify similar threats in the future. What is the suspicious email address that sent the attachment?
We simply earch for the field “Sender: ” Answer:
Q2. The ransomware was identified as part of a known malware family. Determining its family name can provide critical insights into its behavior and remediation strategies. What is the family name of the ransomware identified during the investigation?
We can submit the .eml file to Triage directly. It will extract the binary attachment as well, and also identify the malware family
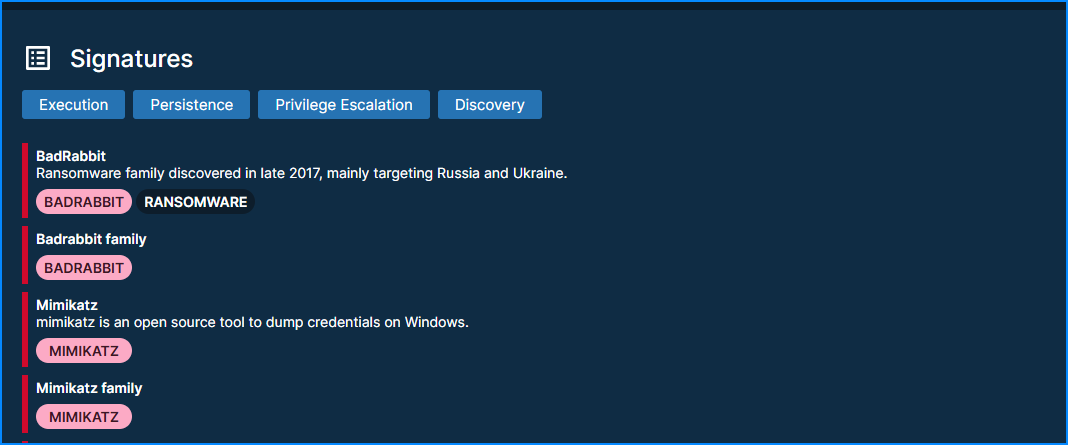
Answer:
- Badrabbit
Q3. Upon execution, the ransomware dropped a file onto the compromised system to initiate its payload. Identifying this file is essential for understanding its infection process. What is the name of the first file dropped by the ransomware?
In the processes list of Triage we can see the first one running a dat file
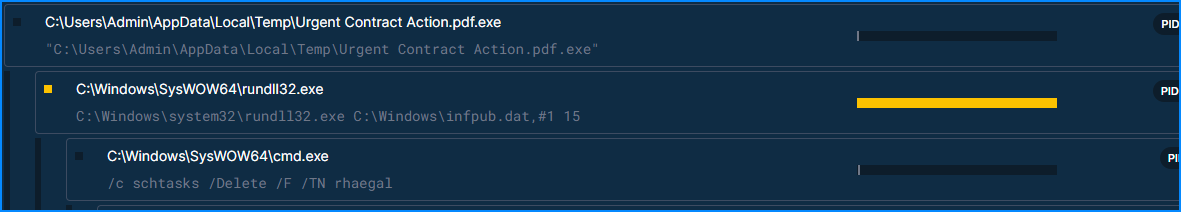
Answer
- infpub.dat
Q4. Inside the dropped file, the malware contained hardcoded artifacts, including usernames and passwords that could provide clues about its origins or configuration. What is the only person’s username found within the dropped file?
From the report in Triage we see in the downloads part that the infpub.dat file, which is a DLL, is there, there are 3 versions, but one is zeroized by the malware.
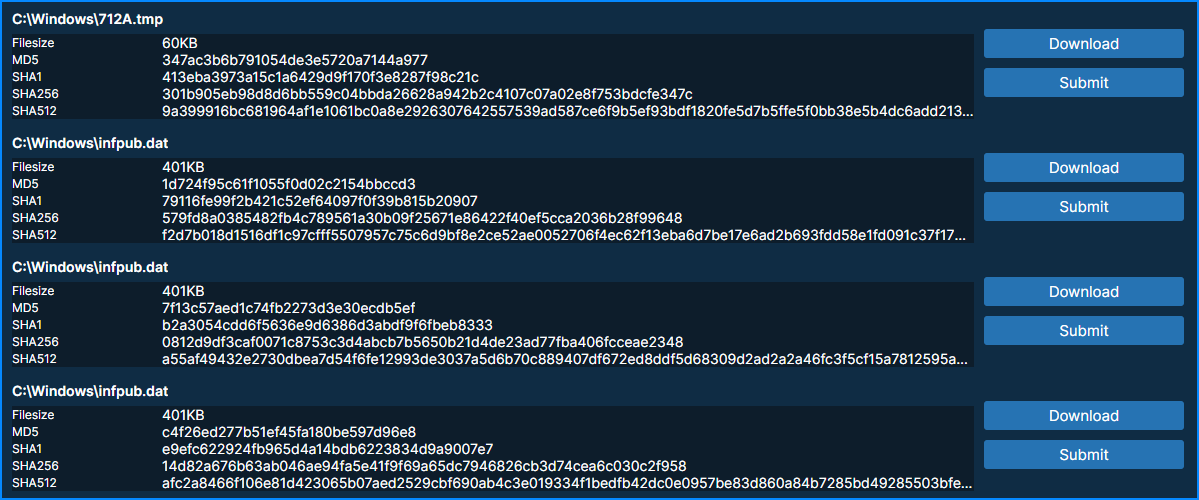
The good one is the one with SHA256: 579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648
We can download that binary and try to find the hardcoded strings.
With strings command in Linux we don’t get all the words in the binary, don’t know why. In Virustotal in the content tab, it’s not everything either.
The quickest way to extract all the strings correctly would be using [bstrings](https://ericzimmerman.github.io/#!index.md from Eric Zimmerman. Awesome tool that will do the job.
Use bstrings in Windows to extract all strings
bstrings.exe -f .\579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648 > strings.txt
Then we look at the strings and we find a list of usernames from some kind of dictionary. There we see the 4 letter word for a person’s name
Another option would be using rabin2 tool from [radare2]https://github.com/radareorg/radare2
rabin2 is installed with R2 and will get all the strings from the data section of the binary:
rabin2 -z 579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648 | cat
And there we will find the username:
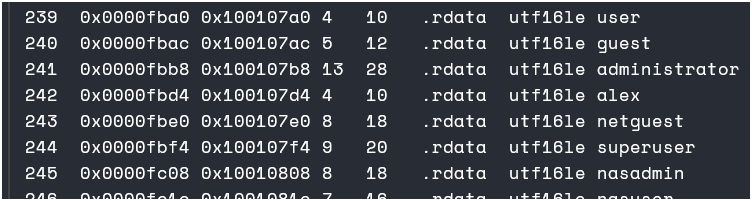
Also, as the answer starts with an ‘a’ and has 4 characters, I can grep for it:
rabin2 -z 579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648 | grep -o '\ba[a-zA-Z]\{3\}\b’
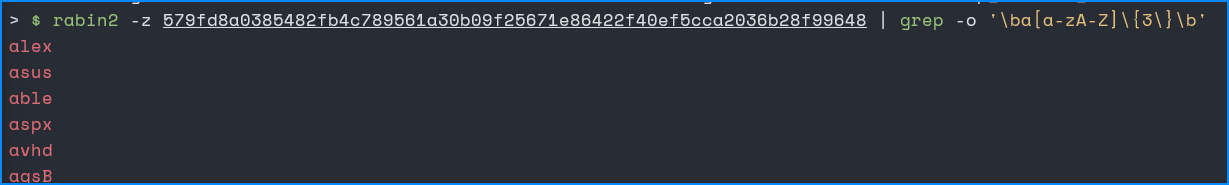
Answer:
- alex
Q5. After execution, the ransomware communicated with a C2 server. Recognizing its communication techniques can assist in mitigation. What MITRE ATT&CK sub-technique describes the ransomware’s use of web protocols for sending and receiving data?
Easy to find on MITRE site, [Application Layer Protocol: Web Protocols]https://attack.mitre.org/techniques/T1071/001/
Answer:
- T1071.001
Q6. Persistence mechanisms are a hallmark of sophisticated ransomware. Identifying how persistence was achieved can aid in recovery and prevention of reinfection. What is the MITRE ATT&CK Sub-Technique ID associated with the ransomware’s persistence technique?
We see a lot of scheduled tasks being created during malware execution in Triage
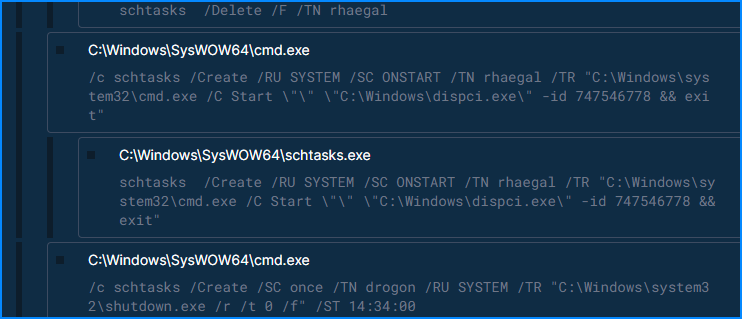
So, likely that’s the ATT&CK technique we are looking for. Answer:
Q7. As part of its infection chain, the ransomware created specific tasks to ensure its continued operation. Recognizing these tasks is crucial for system restoration. What are the names of the tasks created by the ransomware during execution?
From previous question, we see the names for the scheduled tasks
Answer:
- rhaegal, drogon
Q8. the malicious binary
dispci.exedisplayed a suspicious message upon execution, urging users to disable their defenses. This tactic aimed to evade detection and enable the ransomware’s full execution. What suspicious message was displayed in the Console upon executing this binary?
In the relations of the original binary from the attachtment in VirusTotal we can see that one of the dropped files is the one mentioned in the question.
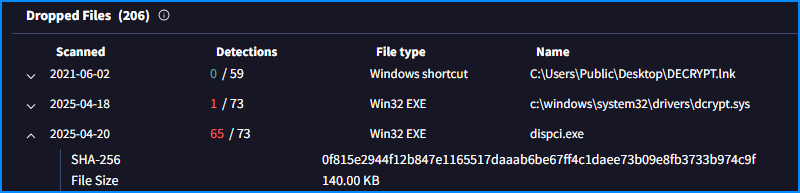
In the comments section we can see the FileScan report that also has the extracted strings and there we can see the message:
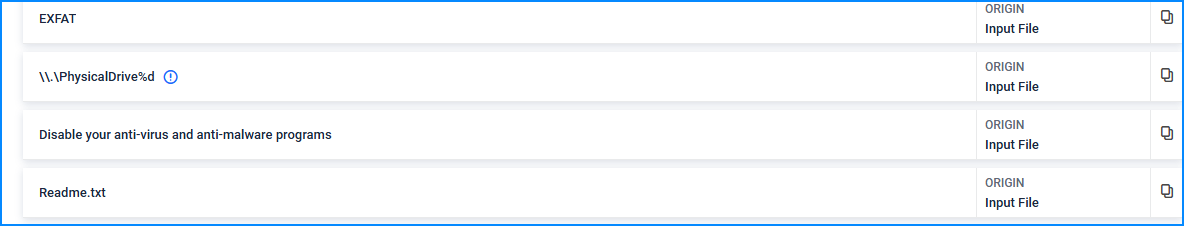
Answer:
- Disable your anti-virus and anti-malware programs
Q9. To modify the Master Boot Record (MBR) and encrypt the victim’s hard drive, the ransomware utilized a specific driver. Recognizing this driver is essential for understanding the encryption mechanism. What is the name of the driver used to encrypt the hard drive and modify the MBR?
We can also see in the relations of the attachment that another dropped file is a driver
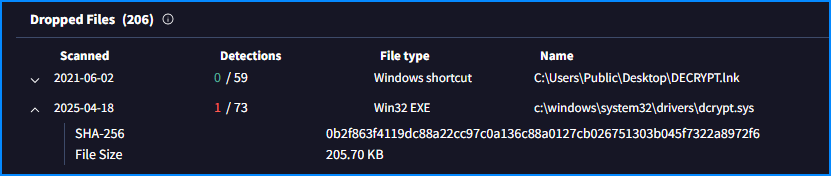
If we check the details of the file in VT, we can see the name of the driver
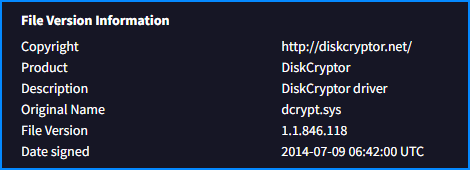
Answer:
- DiskCryptor
Q10. Attribution is key to understanding the threat landscape. The ransomware was tied to a known attack group through its tactics, techniques, and procedures (TTPs). What is the name of the threat actor responsible for this ransomware campaign?
We know the malware is known as BadRabbit, we can search for it in Mitre and see what groups are associated: BadRabbit
And we see the group is
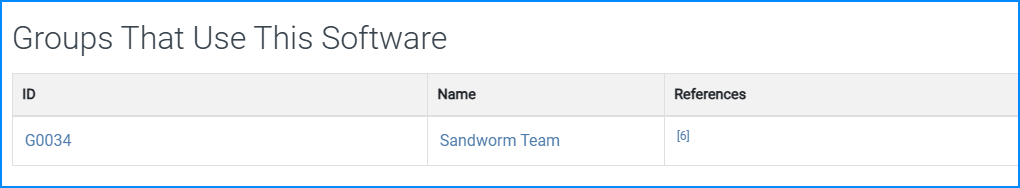
Answer:
- Sandworm
Q11. The ransomware rendered the system unbootable by corrupting critical system components. Identifying the technique used provides insight into its destructive capabilities. What is the MITRE ATT&CK ID for the technique used to corrupt the system firmware and prevent booting?
For this one, in the same BadRabbit entry in MITRE we can see all the TTPs associated, and what is the one for Firmware corruption
Answer:
- T1495